GCP
Ascend Enterprise can be deployed into customer's GCP account. Please see below on what GCP resources Ascend Enterprise requires, how to get Ascend Enterprise deployed and what's the maintenance and access expectations.
Required Resources
Ascend Enterprise (GCP) uses the following GCP services:
- Cloud SQL
- GCE (Google Compute Engine) - this API may need to be enabled before Ascend can be deployed
- GCS (Google Cloud Storage)
- GKE (Google Kubernetes Engine) - this API may need to be enabled before Ascend can be deployed
- IAM
- Load Balancer
Deployment Preparation
This section describes the 5 steps to prepare a dedicated GCP project for the Ascend Enterprise deployment.
Step 1: Create Dedicated GCP Project
Please create a dedicated GCP project within the Organization with the name ascend-io-customer-<customer_name>.
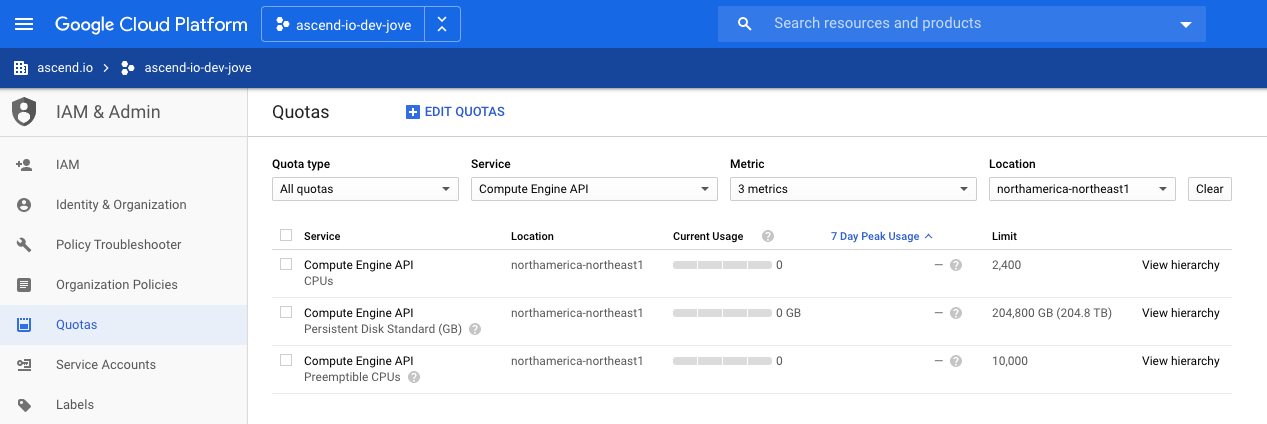
Step 2: Increase Quota
Please request resource quota increases in your desired region for Compute Engine API:
Team Size:
a. Increase “CPUs” limit from 24 to 100
b. Increase “Preemptible CPUs” limit from 24 to 100 (may already be higher)
Standard Size:
a. Increase “CPUs” limit from 24 to 500
b. Increase “Preemptible CPUs” limit from 24 to 500 (may already be higher)
Step 3: Sign Up Support Plan
Please sign up a support a GCP support plan, ideally at the level of “Production” or higher.
Step 4: Grant Ascend Access
Add the [email protected] group to the newly created GCP Project as a Project Editor, Project IAM Admin, Service Networking Admin, Kubernetes Engine Admin, and DNS Administrator.
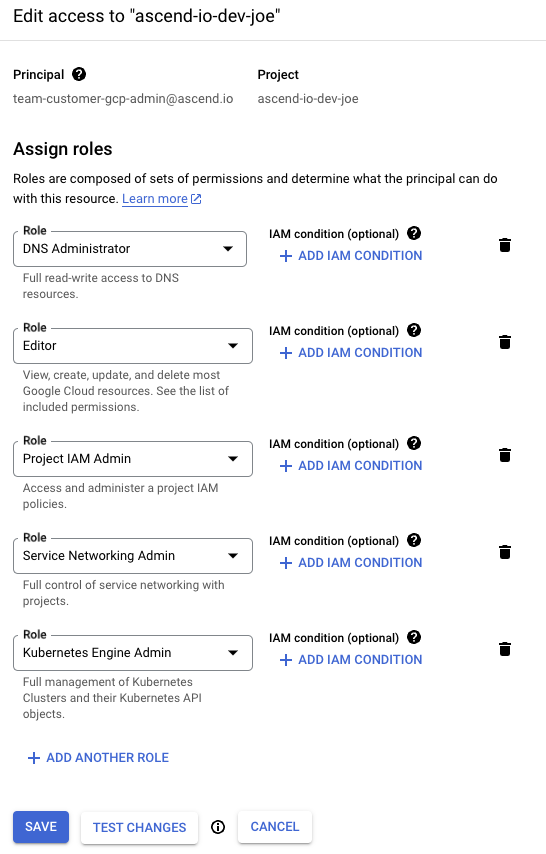
Fine Grained Access
If you need finer-grained access for Ascend, there is a Terraform template available here. Instead of the permissions above, it requests permissions for GKE, Cloud SQL, Compute, Service Networking, DNS, and two custom roles. The custom roles are split into maintenance and provisioning permissions. During standard operations, Ascend only needs the maintenance permissions. However, during certain operations (like significant infrastructure updates), Ascend will require that provisioning permissions be re-instated.
For most customers we recommend using the first method of granting access. However, if you're comfortable in Terraform, feel free to use the provided Terraform template. In order to use it for granting provisioning access:
- Set up a Terraform workspace with the template (if you haven't used Terraform to manage GCP resources before we recommend following this guide). We suggest configuring a remote state backend for persistence of your Terraform state. There's a guide here on how to use GCS for that purpose.
- Run
gcloud auth application-default login --project $PROJECT_ID(replace$PROJECT_IDwith your project ID) - Run
terraform initin your new Terraform workspace directory. - Run
terraform apply -var="project=$PROJECT_ID" -var="region=$REGION"(again, replace$PROJECT_IDand$REGIONwith your project and region, respectively) - Read the Terraform plan output, and when prompted got
Do you want to perform these actions?, typeyesand hitEnter.
After provisioning is complete, you may run terraform apply -var="project=$PROJECT_ID" -var="region=$REGION" -var="enable_provisioning_access=false" to limit Ascend's access.
If Ascend needs access to perform broader updates, first double-check that your Terraform is up to date (you can quickly pull the most recent template by running gsutil cp gs://ascend-io-public/ascend-access.tf main.tf). If the Terraform is not up to date, update your Terraform to use the new template.
Then, simply run terraform apply -var="project=$PROJECT_ID" -var="region=$REGION" (with substituted values, same as above), and approve the plan in order to grant the necessary provisioning permissions.
Step 5: Email Ascend Support
Once the above 4 steps are completed, please send an email to Ascend at [email protected] including the following:
- The Google project ID.
- The desired region for the Ascend Enterprise deployment.
- The desired URL for Ascend Enterprise, e.g. example.ascend.io.
- The desired SSO options, such as Google, Okta, OneLogin, etc. Please follow our documentation for Okta and OneLogin to complete setup.
- Inform us if you need BYON. If you do, please follow these steps.
Deployment Process
Once Ascend receives the email containing the required information, Ascend will proceed with the deployment. This process usually completes within 48 hours after Ascend receives all required information.
Once the deployment has completed, customer will have access to Ascend Enterprise at the preferred URL, e.g. example.ascend.io.
Maintenance & GCP Project Access
Ascend will be responsible for new software releases and maintenance of all services within this GCP project.
Ascend Access
Ascend infrastructure team require access to the GCP project at all times to ensure reliability, performance, and code deployments.
Customer Access
Customer will also retain access to this GCP project for auditing purposes. Ascend does not recommend customer to host any other services in this GCP project other than Ascend Enterprise.
Updated 8 months ago