GCP ByoVPC
Bring your own VPC
Prerequisites
Must be an Enterprise Customer.
Requirements
- All Subnets require unrestricted egress access to
0.0.0.0/0. - Subnet must have private ip Google access enabled.
- Primary IP range of the subnet defines the number of nodes you can have—we recommend allocating a
/24for nodes to provide plenty of room for future expansion (256 hosts max). Allocating a/22allows room for expansion to support all future use cases. We recommend against allocating less than a/27for your nodes because it restricts room for expansion. - The subnet must have a secondary IP range for pods that is 256 times larger than the node IP range (so for a
/24node IP range, the pod IP range would be/16). This is required because GKE uses 256 IPs per node. Ascend configures GKE to support up to 110 pods per node. - The subnet must have a
/24secondary IP range for services. - You must identify a
/28IP range for the GKE control plane (this will be allocated by Ascend when your environment is provisioned). You do not need to allocate a subnet for this in your VPC, Ascend only needs this information for configuration purposes.
Shared VPC
Shared VPC TerminologyIn the Shared VPC details below, we are using GCP's terminology for referencing the relevant resources. The most relevant distinction is:
- Client Project - This is the project that Ascend is installed into.
- Host Project - This is the project where the Shared VPC lives.
Find Service Account Names
- In order to calculate the Service Account names for the internal GCP Service Accounts, you need to first find the Client Project number. To find that, expand the left navigation bar and click on
Cloud overview > Dashboard
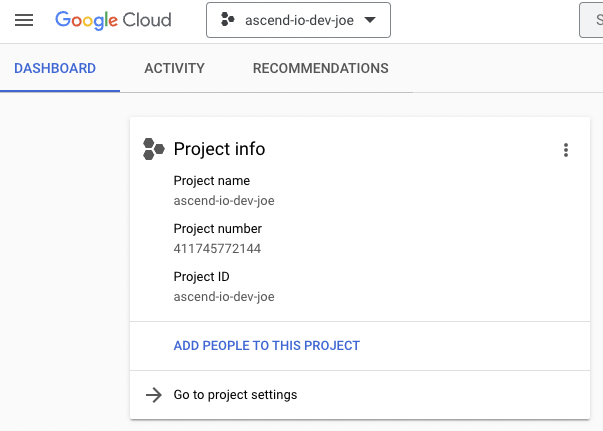
- In the
Project Infocard you will find theProject number. This value will be referred to in the instructions asCLIENT_PROJECT_NUMBER.
Requirements
- In addition to the standard information we need for install, for Shared VPC installation we also need the name of the Shared VPC host project.
- Service Networking API must be enabled on the Shared VPC host project.
[email protected]must be grantedCompute Network Userin the Host Project.- The GKE Service Account from the Client Project must be granted
Compute Network User,Compute Security Admin, andKubernetes Engine Host Service Agent Userin the Host Project. The service account name isservice-CLIENT_PROJECT_NUMBER@container-engine-robot.iam.gserviceaccount.com. - The Google APIs Service Account from the Client Project must be granted
Compute Network Userin the Host Project. The Service Account name is[email protected].
Limited PermissionsIf you're concerned with the permission set in
Compute Security Admin, for the GKE service account, you may construct a custom IAM Role containing the following permissions as described here:
compute.networks.updatePolicycompute.firewalls.listcompute.firewalls.getcompute.firewalls.createcompute.firewalls.updatecompute.firewalls.deleteIf there are any questions regarding the security profile or other details of a Shared VPC setup with GKE, please reference GCP's documentation here.
Connecting to Private Networks
VPC Peering
Summary
To connect Ascend to your private networks, add a peering connection from the Ascend VPC to the network containing your data stores or to a transit VPC.
Limitations
The node, pod, service, and GKE control plane IP ranges must not overlap with any other peered IP ranges. VPC Peering in GCP only supports full mesh routing, so creating a VPC peering connection with overlapping IP ranges isn't possible.
VPN Tunneling
Summary
GCP VPN configuration is more complex than VPC Peering, but it gives you the ability to limit what IP ranges are shared as routable with the rest of your private network. Specifically, you only need to propagate routes for the node IP range. This allows you greater capacity in your Ascend network with a lower impact on consumption of your private IP space.
We recommend reading through GCP's documentation on HA VPN topologies and their documentation on NAT solutions for pod CIDR ranges in GKE.
We support any of these VPN solutions (VPN tunnels to a transit VPC, VPN tunnels directly to an on-prem network, etc).
Limitations
VPN setups are complex, susceptible to misconfiguration, and harder to debug than VPC peering setups. If you have sufficient IP capacity in your network, we recommend using the VPC peering setup.
Requirements
In both VPN and VPC Peering setups, there may not be any overlap between the IP ranges you provision for Ascend and the IPs of the data stores that you wish to access from Ascend. Additionally, traffic must be permitted from the node IP range to the data stores you wish to access from Ascend.
Info for install
- network_name
- subnetwork_name
- pod_secondary_range_name
- services_secondary_range_name
- gke_control_plane_cidr
Shared VPC info for install
- shared_vpc_project_name
VPN-specific info for install
- router_name (router is required in VPN setup for BGP announcements and the actual tunnels)
Table of valid subnet ranges
| Max DFCs | ~500 | ~1k | ~2k | ~4k | ~8k | ~16k |
| Nodes | /24 | /23 | /22 | /21 | /20 | /19 |
| Pods | /16 | /15 | /14 | /13 | /12 | /11 |
| Services | /24 | /24 | /24 | /24 | /24 | /24 |
| Control Plane | /28 | /28 | /28 | /28 | /28 | /28 |
Updated 8 months ago